APT31 Today: When Trusted Cloud Infrastructure Becomes the Attack Surface
- December 7, 2025
- 5 mins
- Apt
TL’DR
APT31 is winning by abusing trust — Microsoft Dev Tunnels, cloud storage, and signed binaries become covert C2 paths that look like normal enterprise traffic.
MITRE ATT&CK Coverage at a Glance
| Tactic | Techniques | Spotlight |
|---|---|---|
| Initial Access | Phishing; exploit of public-facing applications | — |
| Execution | User execution | — |
| Persistence | Scheduled task or job | Deep dive |
| Discovery | File and directory discovery; browser credential access; network service discovery; local system data; account discovery | — |
| Credential Access | Keylogging; OS credential dumping | — |
| Lateral Movement | RDP; pass-the-hash; lateral tool transfer | — |
| Command and Control | Internal proxy; ingress tool transfer; web service (cloud C2); non-standard ports; encrypted channels; multi-hop proxy | Deep dive |
| Defense Evasion | DLL sideloading; obfuscated files; multi-hop proxy via developer tooling | New technique focus |
| Exfiltration | Exfiltration to cloud storage | — |
Deep Dive: Defense Evasion by Abusing Microsoft Trust
Technique: Multi-hop Proxy via Microsoft Dev Tunnels
MITRE: Defense Evasion, Command and Control
APT31 abused Microsoft Dev Tunnels, a legitimate feature used by Visual Studio and VS Code, to establish a covert and highly resilient C2 channel.
How It Works
- The infected host establishes an outbound encrypted connection to Microsoft-owned infrastructure
- Traffic flows through a Microsoft-hosted Dev Tunnel endpoint
- The attacker accesses the tunnel from the other side, gaining interactive control
From the defender’s perspective:
- The destination is a trusted Microsoft domain
- The protocol is standard HTTPS over port 443
- The traffic pattern resembles normal developer activity
This effectively removes the attacker’s infrastructure from direct visibility and shifts detection responsibility onto behavioral analysis, not network reputation.
Related Defense Evasion and C2 Techniques
Cloud C2 via Legitimate Web Services
APT31 also relied on cloud storage platforms such as OneDrive, Dropbox, and Yandex.Cloud to host payloads and retrieve commands.
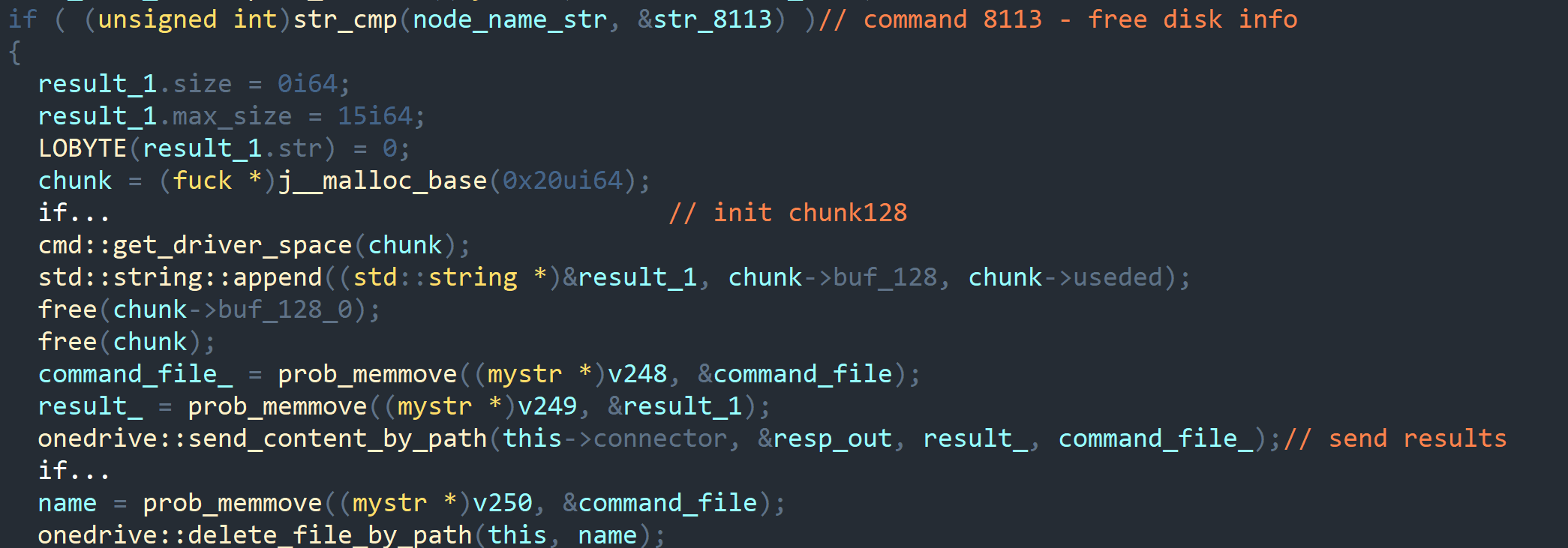
This approach mirrors the Dev Tunnel strategy:
- Trusted platforms
- Encrypted traffic
- Blending with normal enterprise usage
Cloud services become both delivery mechanism and command channel.
DLL Sideloading via Signed Microsoft Binaries
APT31 delivered malware using phishing lures that launched a legitimate signed executable vulnerable to DLL sideloading.
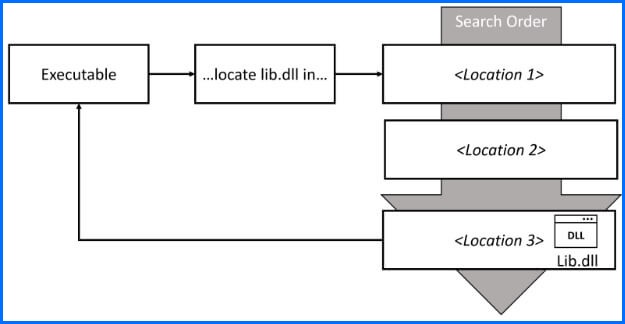
A malicious .lnk file triggered execution of BsSndRpt64.exe, which then loaded the attacker-controlled BugSplatRc64.dll. The malware inherited the trust and legitimacy of the signed binary, bypassing basic application controls.
Persistence Through Hidden Scheduled Tasks
To maintain access, APT31 created scheduled tasks with names resembling legitimate software, then deliberately hid them by removing the task’s SecurityDescriptor from the registry.


The task continued to execute normally while remaining invisible to standard Windows management tools.
Why This Matters
- Trust relationships are now primary attack vectors
- Cloud platforms are operational infrastructure for attackers
- C2 no longer requires attacker-owned servers
- Detection failures increasingly stem from assumed legitimacy
This is not a vulnerability problem. It is a trust and visibility problem.
Takeaways
For all teams: Cloud services, developer tooling, and signed binaries are now active attack surfaces.
For red teams: This is a playbook for abusing trust, workflows, and platform legitimacy.
For defenders: Focus on behavioral anomalies, not domain reputation or IP allowlists.